

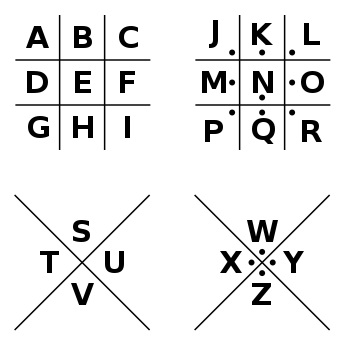
The Pigpen Cipher, also known as the Pigpen Cipher, is a substitution cipher used to encrypt and decrypt secret messages. It derives its name from its distinctive grid-like shape, which resembles the enclosures or pens used for pigs on farms.
The origins of the Pigpen Cipher are shrouded in mystery, but it is believed to have been in use as early as the 18th century. It gained prominence during the Renaissance and found frequent use among secret societies like the Freemasons.
The Pigpen Cipher employs a grid composed of vertical and horizontal lines, with each letter of the alphabet assigned a specific geometric shape. These letters are positioned within the grid, and the corresponding shape serves as the substitute in the encrypted message.
To encrypt a message using pigpen simple copy down the part of the cipher key grid corresponding to the letter.
Here is the word 'hello' encrypted into pigpen:
What word is encrypted using Pigpen??
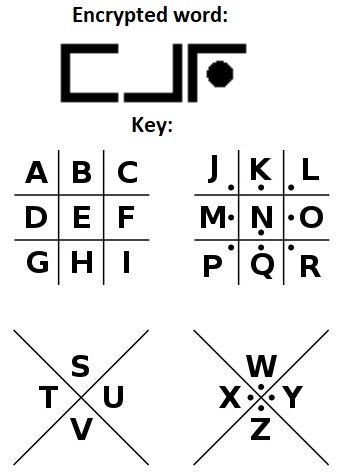
What is the word encrypted with pigpen?
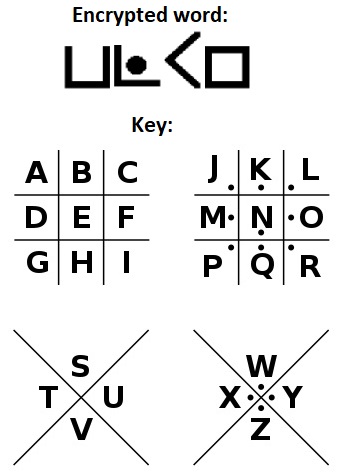
What is an advantage of using the Pigpen cipher?
The Pigpen Cipher is highly vulnerable to several cryptographic attacks due to its simple substitution nature. Here are the most effective attacks:
The Pigpen cipher has a distinct look, making it easy to recognize.
Once identified, decryption is straightforward by matching symbols to the standard Pigpen grid.
Since Pigpen is a monoalphabetic substitution cipher, each letter in the plaintext is always replaced with the same symbol. Common letters in English (like E, T, A, O) will appear most frequently in the ciphertext, making it possible to map symbols to letters.
If the exact Pigpen variation is unknown, a brute force attack can test different Pigpen grids and orientations. Since there are only a few possible symbol arrangements, it’s easy to break.
What is a disadvantage of using the Pigpen cipher?
Cryptanalysis